
case study
DevSecOps Pipeline
Creating a security focussed pipeline using company standard tooling.


The Brief
The infrastructure deployment to AWS at Luminus required a security focussed pipeline using company standard tooling – Terraform code
scanned by Tenable to deploy security approved infrastructure every time.
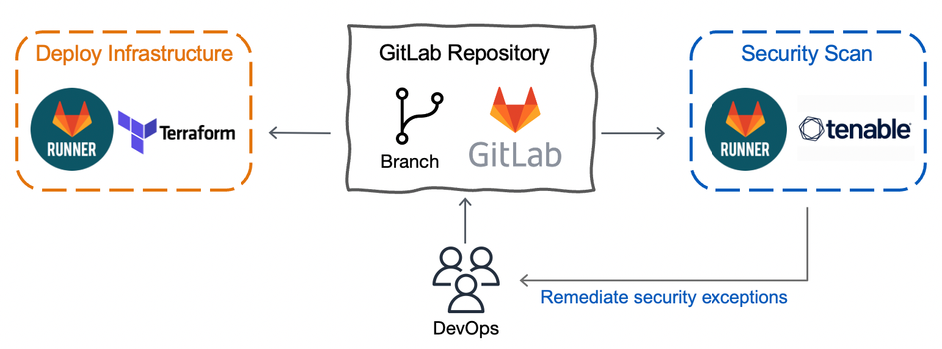
Automated & Secure Infrastructure Deployment
Deploying infrastructure at Luminus needed to be automated while ensuring the resources created aligned with the company security standards and AWS best practices.
Creating GitLab runners on AWS infrastructure created a secure system to deploy Infrastructure-as-Code through automation while
maintaining control of the environment running the terraform. This foundation of standardised GitLab pipelines allowed integration with Tenable. All code on deployment is scanned for any security violations outside Luminus standards and the AWS best practice frameworks.
GitLab & AWS Security
The Tenable integration with GitLab provides a system for developers to have their IaC scanned and any issues immediately raised within GitLab which the developer can review and remediate immediately. This not only helps developers ensure what they are deploying is up to standard but also prevents any unsuitable code from going live.
In Production and Acceptance environments pipelines will be blocked from running if any detected violations are categorised as high risk.
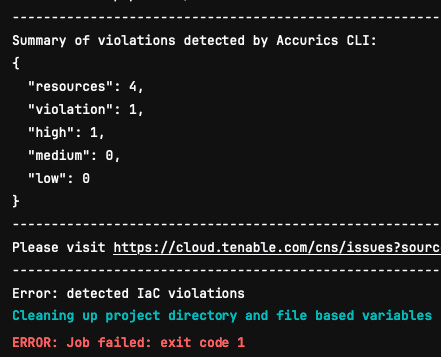
High violations force a failure of the pipeline until the code is updated to resolve the issues created in the GitLab repository.
High violations force a failure of the pipeline until the code is updated to resolve the issues created in the GitLab repository.

Keeping this segregation of duties ensures a divide between the developer and the security tools while allowing for quick remediation as the developer can scan code, check issues and fix issues all through an automated process without any need to have access to security tools or any involvement of security personnel.
GitFlow Workflow Overview
The pipelines leverages the GitFlow workflow with automated pipelines for AWS resource deployment.
The GitLab access is split into three levels:
Access Role
Purpose
1.
Owner
Full access to all GitLab and pipeline features
2.
Maintainer
Full code push, merging and pipeline access.
3.
Developer
Full code access but can’t merge to the main branch – only submit for approval to Maintainer/Owner.
The roles are attached to AD groups for SSO; all authentication and access controlled through Luminus AD controls.
General GitFlow overview with GitLab pipeline
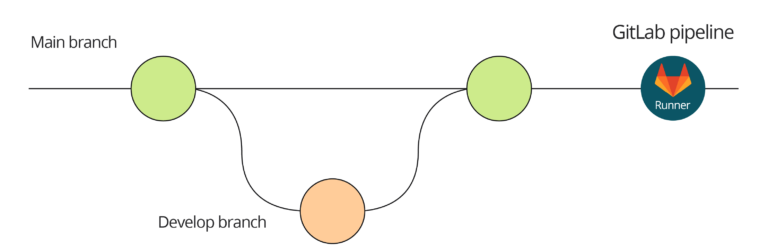
The Main Branch:
- Contains the official release history.
- Is protected from direct commits.
The Develop Branch(es):
- Are sourced directly from the main branch.
- Are used to build & test new features.
The GitLab Pipeline:
- Is triggered by commits to the main branch.
- Is integrated with Tenable for code scanning.
- Can automatically deploy the IaC into the appropriate environment.
Gitflow workflow:
- 1. A Developer creates a new branch from main to make changes to the IaC code.
- 2. When ready the Developer requests to merge the code back into the Main branch.
- 3. The Maintainer reviews and approves the merge request.
- 4. The code is committed to the main branch.
- 5. The commit to the main branch triggers the pipeline.
Automated Security Scanning
Code goes through security scanning before GitLab pipeline deploys infrastructure. The pipeline is integrated with Tenable which checks the code against the Tenable Cloud Security Policies and the AWS Well-Architected Framework.
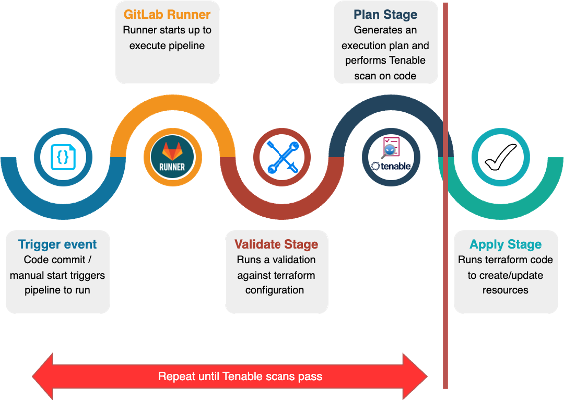
Remediation and Deployment of Infra via Terraform
The GitLab pipeline performs the following steps:
- 1. Validates the terraform code.
- 2. Generates an execution plan.
- 3. Tenable scans the code.
- 4. A vulnerability report is generated.
- 5. Depending on the environment and the severity of the findings the pipeline may be blocked.
- 6. The Developer remediates any security exceptions.
- 7. The corrected code is checked into GitLab and the pipeline runs again.
- 8. The security scan now passes.
- 9. The infrastructure is deployed with Terraform!
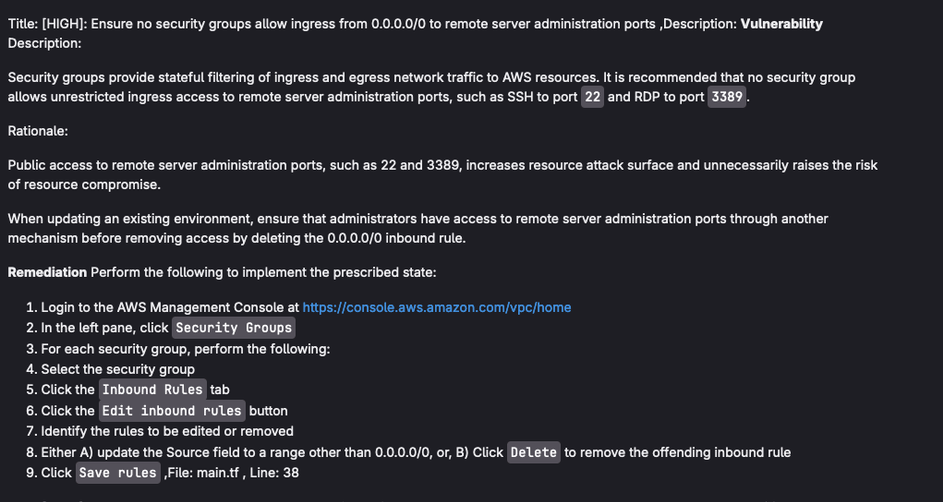
On merge to protected branch - show an exception that is AWS Specific, e.g. rdp access from anywhere!

DevSecOps Benefits
- Security posture is continually enforced ensuring compliance.
- Increases agility and speed to market reducing potential security incidents.
- Automated scanning and deployment enforces DevSecOps and Gitflow compliance.
- Improved traceability, auditability and accountability.
Meet the Team


Moldir Baimagambetova,
Consultant and DevOps Engineer
Moldir oversees the creation, testing, and enhancement of the Terraform code necessary for establishing the Aligne infrastructure. She has also connected the Terraform GitLab code repositories to GitLab DevSecOps pipelines, guaranteeing the detection of any security weaknesses prior to the actual infrastructure deployment.
Scott is responsible for the build and support of the GitLab pipeline configuration used to deploy infrastructure at Luminus.
He created a standardised format for the DevSecOps pipeline to ensure both Application and Security teams could get what they needed for automated IaC deployments.

Scott Noon,
Consultant & DevOps Engineer

Moldir Baimagambetova,
Consultant and DevOps Engineer
Moldir oversees the creation, testing, and enhancement of the Terraform code necessary for establishing the Aligne infrastructure. She has also connected the Terraform GitLab code repositories to GitLab DevSecOps pipelines, guaranteeing the detection of any security weaknesses prior to the actual infrastructure deployment.

Scott Noon,
Consultant & DevOps Engineer
Scott is responsible for the build and support of the GitLab pipeline configuration used to deploy infrastructure at Luminus.
He created a standardised format for the DevSecOps pipeline to ensure both Application and Security teams could get what they needed for automated IaC deployments.
contact us
Contact the Team for more information on our case studies and how we can help your company with its cloud transformation.

Click the button below for more information on our services and solutions
